The fact that various difficulties were brought with COVID-19 in 2020 drove corporations toward remote staff and cloud-based technologies where information vulnerability created a massive need for companies to improve their cyber assets or risk data loss and increment costs.
In this article, you’ll discover more about the two main reasons why the Internet urgently needs a P2P global network and the best alternative that implements this innovative technology.
Feature 1: Internet Security
Cybercrime has increased by 600% due to the COVID-19 pandemic. Fraudsters have boosted the use of sophisticated email, mobile, and computer malware armed with the knowledge that people spend more time on their electronic devices.
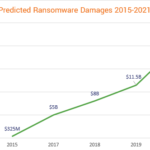
Undoubtedly, with the introduction of machine learning and tailored spear-phishing emails, malware attacks have become increasingly sophisticated, which generates the need to implement a P2P network to overcome. The chart below shows this tendency as well:
Source: The SSL Store
Let’s see each section in more detail.
1) Email Malware
An email malware is a harmful code spread in electronic mail and can be activated when a user clicks on a link, opens an email attachment, or interacts with the infected message in some other way.
According to Purplesec 2021 Cyber Security Report, malware is sent through email in 92% of cases, so knowing how to recognize it can prevent being scammed in a non-P2P network architecture. The following are some “red flags” that suggest an email may contain malware:
1. Suspicious sender’s email address: If the sender’s email address is unknown or does not match an expected address for a corporation, it’s likely a malware email.
2. Your username appears in the email topic or attachment: A virus email’s subject box may contain your username or be blank. Your username could be included in the filename of malicious attachments.
3. Malware emails frequently include the words “warning,” “danger,” or “urgency” to entice recipients to respond hastily before they have had enough time to consider their options. If you receive an email that asks you to download a file to remedy an issue, be cautious.
2) Mobile Malware
Mobile malware is malicious software meant to attack mobile devices such as smartphones and tablets to obtain personal information.
According to Purplesec, the number of new malware types for mobile devices surged by 54% in 2018, which could arguably be prevented using a P2P open network.
Here are some security tips for avoiding mobile malware:
1. Connect to a secure Wi-Fi network: When people access their private data in public places, like an airport with free Wi-Fi, the data may be accessible to criminal users sniffing wireless traffic at the same point of access.
2. Prevent Jailbreaking: Jailbreaking means breaking the device’s security model and allowing all apps, including malicious ones, to access the data owned by other apps.
3. Encrypt your devices: It makes it extremely hard for someone to break and steal data by protecting your gadgets by fully encrypting the device. Setting the device and the SIM card with a secure password is essential.
3) Computer Malware
Have you ever noticed strange cases of image pixelation or random windows popping up on your screen? Or maybe you heard weird sounds? If your answer is yes, there is a high chance that malware or virus may have invaded your machine, making the use of a P2P virtual network urgently required.
According to Purplesec, macOS malware grew 165% over the last year, and Windows development rates for malware dropped from an all-time high to 11.6%.
However, there are precautions you can take to avoid this kind of malware:
1. Update your antivirus: You must make sure that your apps, antivirus software, and operating system are up to date to prevent your computer from becoming infected.
2. Automatic virus scanning: Your antivirus software should contain automated functions allowing continuous scanning of your machine against viruses and performing cleanup.
3. Reboot in safe mode: Safely starting your computer offers you the opportunity to run your antivirus program and look more closely at the (potential) problem.
Feature 2: Decentralized Data
There are several examples of massive sales of data from major technology companies to third parties previously seen, making it urgent that data is spread in a fully decentralized internet now.
When someone provides personal information to a company or any governmental entity, most people do not understand how it is used and stored nowadays, which produces concerns about the potential risks that data can suffer when stored in centralized data centers.
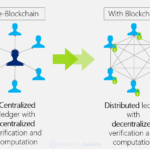
Let’s see the differences between centralized and P2P open network.
Source: Research Gate
1) Centralized Data Storage
Did you know that 80% of the world’s data currently resides in hyperscale data centers in central locations concentrated in 20 companies?
Centralized data storage systems are built on a central server where authorized persons can manage the information to make possible data traceability.
One of the most significant disadvantages of centralized data storage is that it has deficient privacy standards, making it easier for third-party participants to access data through hacks.
2) Decentralized Data Storage
A decentralized cloud crypto strategy involves using several separate devices linked to the network, supplied by various nodes. These nodes retain autonomous control, which allows each of them to determine its criteria for the availability of data workload.
A P2P network offers increasing data privacy and transparency, reducing processing needs which drastically decrease resource usage, making it cheaper to run within the decentralized web.
After describing these two essential features that the Internet must have now, we firmly believe that ThreeFold is the best alternative to make a more secure, decentralized, and sovereign internet.
ThreeFold Is the Best Solution to Have a Fully Peer-to-Peer and Secure Internet
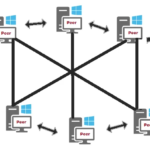
ThreeFold is a peer-to-peer cloud storage solution granting substantial energy efficiency compared to existing data storage systems while letting information be 100% secure, private, and available 24/7 without exception.
Source: Digital Thinker Help
This fully decentralized platform improves:
1) Network Security
To close the enormous security gap in data centers nowadays, the ThreeFold P2P virtual network has developed its operating system called Zero-OS, which runs on the nodes. Every node is linked inside a specified network and has its iPv4 or iPv6 address, which keeps the information 100% encrypted and private to the user.
Also, the Peer-to-Peer Network uses a web gateway mechanism that allows the exposure of services to the open internet without allowing incoming connections to keep applications and storage secure at all times. This means there is no incoming TCP/IP traffic allowed from the outside.
2) Network Efficiency & Scalability
ThreeFold’s Peer-to-Peer Network was designed to find the shortest possible path between peers and encrypt the end-to-end connection. It allows for peer-to-peer links like in meshed wireless networks. This is very different from consensus mechanisms like distributed blockchains which use more networks than centralized networks.
When you download the same file from a peer-to-peer network, using a BitTorrent platform as a starting point, the download is performed differently. The file is downloaded to your computer in bits and parts from many other computers connected to the same P2P network and already have that file or at least parts of it. At the same time, the file is also sent (uploaded) from your computer to other devices that are asking for it. This situation is similar to a two-way road: the file is like multiple small cars coming to your PC while also leaving to others when it is requested.
When it comes to file-sharing, the larger a P2P network is, the faster it is. Having the same file stored on many of the peers in a P2P network means that when someone needs to download it, the file is downloaded from multiple locations simultaneously. Peer-to-peer networks are incredibly scalable. Adding new peers is easy as you don’t need to do any central configuration on a central server.
3) Centralized Data & Points of Failure
Nowadays, the centralized data issue is not the only problem that information management is facing. There are also central points of failure in the system, which leads to sporadic shutdowns that sometimes can last minutes and even hours.
To overcome today’s colossal data centralization gap, ThreeFold has created the most optimized peer-to-peer cloud network, bringing privacy by design. All data and applications remain under the user’s control.
Therefore, a P2P global network, such as the one offered by ThreeFold, stimulates equality by blocking a substantial amount of single-player data accumulation and also eliminates the possibility of making websites around the world to be disconnected because of the internet shutdowns.