Every passing day, Blockchain technology brings technological capabilities and opportunities continuously that certainly bring change in every sector. Even with our best efforts to keep informed, the field persistently astounds with improvements. Have you ever questioned what underpins this trend of blockchain solutions? The answer resides with consensus algorithms.
Consensus algorithms underpin each blockchain’s agreement process. With millions cooperating within the same digital world, one may ponder how cooperation occurs without conflict. The solution stems from the carefully engineered design of the blockchain network, with consensus algorithms playing a pivotal part. Gaining knowledge about how blockchain reaches agreement on new blocks necessitates further study.
This guide intends to offer a thorough understanding of the processes of consensus algorithms. Let us start on this insightful adventure!
What are Consensus Algorithms?
A consensus algorithm refers to the process used by nodes or miners on a blockchain network to agree on the valid state of the distributed ledger. As there is no central authority, nodes need a way to coordinate with each other to validate transactions and agree on the chronological order of blocks being added to the chain.
Consensus algorithms enable the nodes on a decentralized blockchain network to work together, stay synchronized, and avoid disputes regarding the authentic state of the ledger.
Some key functions performed by consensus algorithms include:
1) Transaction validation
Checking that transactions are valid, not duplicated or fraudulent before adding to the ledger. This prevents double-spending.
2) Block validation
Verifying that new blocks contain valid transactions and conform to network rules before adding to the chain.
3) Agreement
Facilitating coordination between nodes so that they agree on the order and chronology of block additions to the chain.
There are different types of consensus mechanisms used by various blockchain platforms and cryptocurrencies.
Let’s examine some of the most popular ones:
Types of Consensus Algorithms
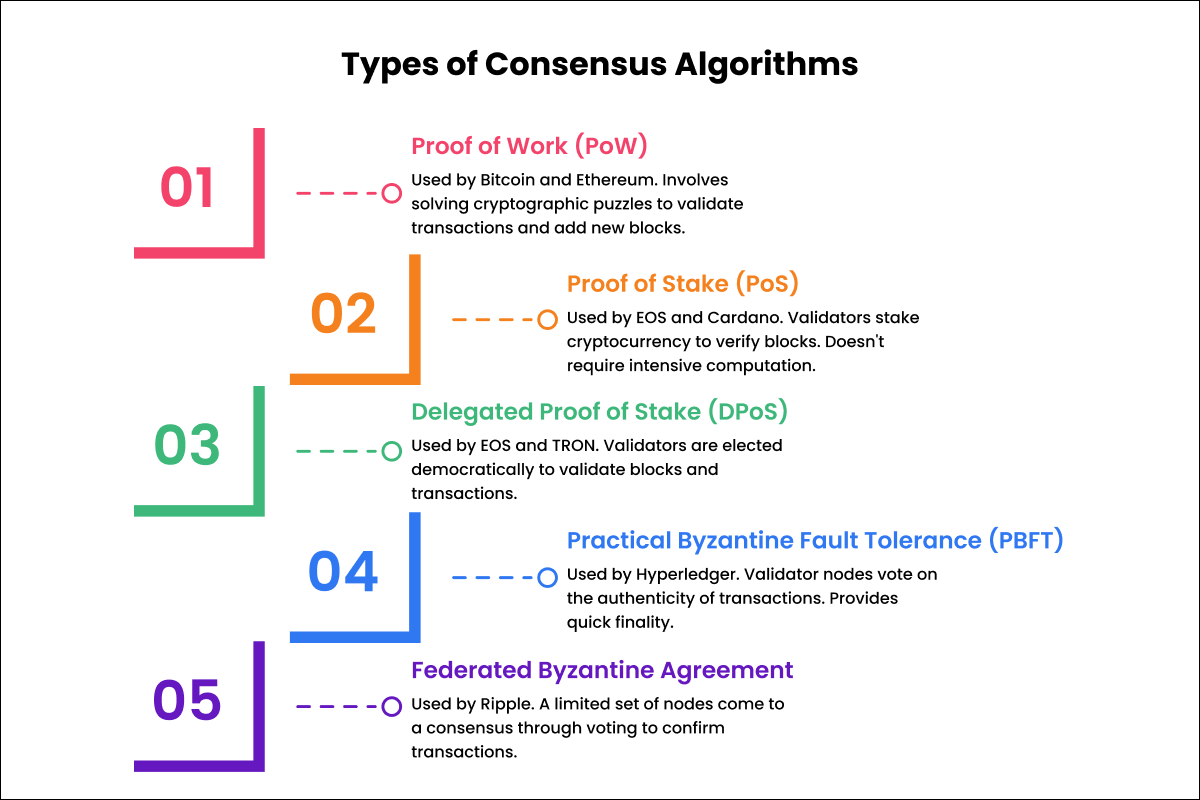
Comparison of different consensus mechanisms
As we can see, each consensus algorithm has its strengths and weaknesses based on factors like security, scalability, decentralization, and computational requirements. The right consensus depends on the specific use case of the blockchain application.
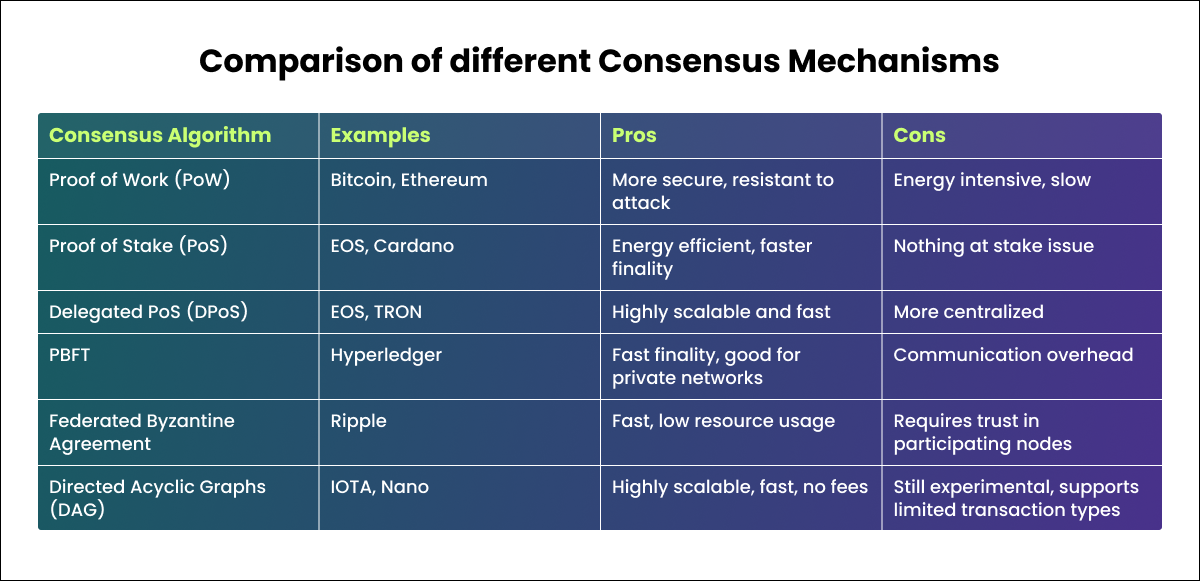
Now let’s look at two of the most popular consensus algorithms – Proof of Work and Proof of Stake – in a bit more detail.
What is Proof of Work?
Proof of Work (PoW) was the first consensus algorithm implemented for blockchain by Bitcoin. It involves miners competing to solve cryptographic puzzles to validate transactions and create new blocks. Solving the puzzle requires brute computational effort and processing power.
When a miner solves the puzzle correctly, they get the right to add a new block of transactions to the blockchain. The miner is rewarded for their efforts with cryptocurrency.
How Proof of Work (PoW) Works
Here is a step-by-step overview of how PoW consensus works:
- Transactions are broadcast to the peer-to-peer network consisting of miners.
- Miners collect transactions into a block. This block also contains a cryptographic hash pointer that links to the previous block.
- Miners try to determine a nonce value that can generate a hash value meeting certain difficulty criterion when combined with the block data.
- Miners randomly guess different nonce values and calculate the hash repeatedly, until one of them finds a valid nonce that satisfies the difficulty target.
- The lucky miner who finds the nonce first broadcasts the block to other nodes in the network.
Pros of Proof of Work
Security: PoW is very secure against attacks and tampering due to the high amounts of computational work required to overwrite historical blocks and recalculate the associated nonce values.
Simplified verification: Nodes can easily verify the PoW done by miners before accepting valid blocks. This light verification keeps the network decentralized.
No need for trusted nodes: The difficulty and cost of PoW ensure that influencing consensus requires a majority of the network’s compute power, making collusion infeasible.
Cons of Proof of Work
Energy intensive: The computational workload and electrical energy required for PoW mining is very high. This drives up costs and environmental impact.
Hardware centralization: Specialized ASIC mining rigs that afford economies of scale tend to earn a higher proportion of rewards, leading to some centralization among miners.
Slow: Only one valid nonce is found every ~10 minutes in Bitcoin. Confirmation of transactions takes time due to the low block generation rate.
Susceptible to 51% attack: If a single miner gains over 50% of compute power, they can manipulate consensus and double-spend coins.
What is Proof of Stake (PoS)?
Proof of Stake (PoS) takes a different approach to the consensus that is far more energy efficient than PoW mining. Instead of miners, PoS leverages validators who stake their coins to verify transactions and create blocks. The more coins they stake, the greater their chances of being selected to propose the next block.
Unlike PoW mining, staking doesn’t require massive computing power because blocks are forged (validated) based on the validator’s stake in the network rather than puzzle-solving.
How Proof of Stake (PoS) Works
Here is an overview of the PoS consensus process:
- Validators stake their coins by depositing them into specially configured wallets.
- The protocol selects certain validators based on criteria like staked amount, randomness, etc. to propose and validate new blocks.
- The chosen validators verify the transactions in their blocks.
- They sign and broadcast their blocks to the network for confirmation by other validators.
- Validators reach consensus through voting. Blocks that receive majority votes are added to the chain while their creators earn the transaction fees.
- The process repeats with new validators selected to forge each block.
- Validators can have their stake slashed if they act maliciously or go offline frequently.
Pros of Proof of Stake
Energy efficient: No compute-heavy puzzle solving required. This makes PoS much greener than PoW.
No advanced hardware needed: Ordinary computers are enough to become validators, increasing decentralization.
Economic incentives: Validators are incentivized to act honestly to avoid losing their stake. The rewards also encourage participation.
Scalability: Blocks can be created much faster in PoS since puzzle solving is not a bottleneck.
Cons of Proof of Stake
Nothing at stake problem: Validators might validate forked chains simultaneously to earn more rewards without repercussion.
Might lead to plutocracy: Wealthier validators who can stake more coins have better chances of transaction verification and earning fees.
Susceptible to 51% attack: If a validator gains over 50% stake, they can control consensus and double spend coins.
Requires minimum staking amount: Smaller holders might be barred from staking if the minimum amount is set too high.
Exploring Other Consensus Algorithms
Beyond PoW and PoS, there are other consensus models with unique characteristics. Let’s take a quick look at two prominent examples – PBFT and DPoS:
Practical Byzantine Fault Tolerance
Practical Byzantine Fault Tolerance (PBFT) is a consensus algorithm that offers quick finality through voting. It’s designed to function effectively even if nodes fail or act maliciously. Here’s a quick overview:
– A primary node or leader is elected as the block proposer.
– The leader sends the new block to validator nodes.
– Validators check the block’s transactions and vote on its validity.
– If 2/3rd validators approve, the block is confirmed and finalized.
– If the leader is found malicious, a view change happens and a new leader is elected.
Delegated Proof of Stake (DPoS)
Delegated Proof of Stake (DPoS) is an alternative PoS model where token holders vote to elect ‘delegates’ who validate transactions and propose blocks on their behalf.
– Network participants vote for trusted delegates based on their reputation and expertise.
– The top-ranking delegates are chosen to operate nodes and validate transactions.
– Votes can be changed in real-time by users to exclude malicious actors.
Practical applications and use cases
Beyond PoW and PoS, there are other consensus models with unique characteristics suited for certain applications. For example, PBFT is used in private blockchains for financial settlement between banks and institutions due to its fast finality. The permission nature allows for a controlled participant set. Meanwhile, DPoS has use cases in gaming and entertainment platforms because stakeholders can elect moderators to act as delegates and leverage the high scalability. The ability to vote delegates in and out frequently provides agility. DAG-based consensus is also gaining traction for IoT ecosystems due to its high scalability and zero-fee structure. As we can see, different consensus mechanisms tend to be better fitted for certain blockchain use cases based on their specific properties.
Factors Influencing Consensus Algorithm Selection
Several crucial factors guide the choice of consensus algorithms:
Scalability
The consensus protocol must efficiently scale to handle the required transaction throughput and network size of the blockchain application. PoW scales poorly while PBFT works for up to 20 nodes only. In contrast, DPoS is highly scalable.
Security
The algorithm must provide adequate protection against attacks, especially 51% of attacks. PoW offers the highest security currently but alternatives are being optimised for better protection.
Energy Efficiency
Mining impacts the environment severely so alternatives to compute-heavy PoW are desired. PoS, DPoS, and PBFT drastically reduce energy usage.
Governance Model
Public, open networks like Bitcoin and Ethereum need highly decentralized consensus, whereas PBFT works better for private blockchains. Hybrid models like PoS and DPoS offer more governance flexibility.
Conclusion
Decentralized consensus enables trust and coordination between participants in a blockchain network without requiring a central authority. Consensus algorithms provide the critical foundation that powers blockchain-based cryptocurrencies, finance platforms, games, identity systems, and any application requiring transactional integrity on a distributed ledger.
While PoW pioneered the Nakamoto consensus, its energy and performance limitations have spurred evolution into PoS, DPoS, PBFT, and other algorithms. There is no single perfect consensus mechanism – different algorithms make tradeoffs between scalability, security, speed, decentralization, and computational needs.
Coordination of truth and integrity are enabled on the blockchain through consensus algorithms. These allow participants to agree on even when some nodes encounter issues or behave badly. As blockchain continues advancing, consensus mechanisms must regularly improve to provide the protection, efficient usability, distributed nature, and functioning expected of decentralized applications ahead.