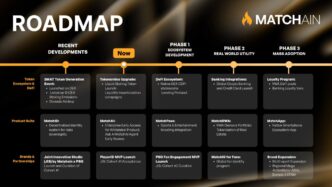
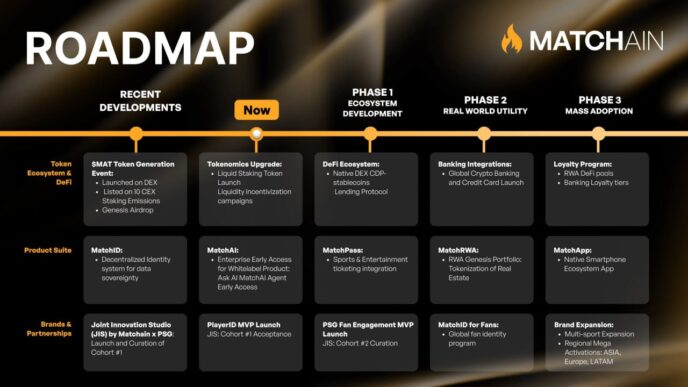
Big news in the cybersecurity world: a massive data breach just happened. We’re talking about over 16 billion login details exposed. This whole thing really shows how bad infostealer malware is getting. It’s a wake-up call for everyone online.
Key Takeaways
- Over 16 billion login credentials were leaked in one big event.
- This data came from 30 different sets, and some info might be duplicated.
- Most of the leaked data is new, not just old stuff recycled.
- Big companies like Google, Facebook, and Apple could be affected.
- Infostealer malware and unsecured cloud databases are a big part of why this happened.
Unprecedented Scale of Recent Security Leaks News
Over 16 Billion Credentials Exposed
Okay, so get this: we’re talking about a security leak of epic proportions. Over 16 billion login credentials have been exposed. That’s, like, more than two credentials for every person on the planet. It’s not just a small spill; it’s a data tsunami. This massive password leak is a compilation of data from various sources, making it a real goldmine for cybercriminals. It’s pretty scary when you think about how much of our lives are online these days.
Impact on Major Digital Platforms
This breach isn’t picky; it hits everything. We’re talking about major social media platforms like Facebook, Google, Telegram, and even Zoom and Twitch. Corporate services like GitHub and various cloud providers aren’t safe either. Even government and financial portals have been compromised. It’s like nobody is immune. The scale of the corporate service exposure is alarming, and it really makes you wonder where your data is safe. It’s a wake-up call for everyone to take their online security seriously.
Fresh Data Fuels New Threats
What makes this leak particularly nasty is that it’s not just old, recycled data. This includes recent logs, which means the information is fresh and more likely to be valid. Infostealer malware is constantly harvesting data in real-time, and new datasets are popping up every few weeks. This constant stream of new data is fueling new threats and making it easier for cybercriminals to launch successful attacks. The fact that infostealer malware is a primary source means the data is current and highly structured, making it even more dangerous. It’s a constant game of cat and mouse, and right now, the criminals seem to be winning.
Understanding the Source of the Security Leaks News
Infostealer Malware as a Primary Vector
So, where’s all this leaked data coming from? Well, a big chunk of it seems to be from infostealer malware. These nasty programs sneak onto your computer and grab all sorts of login details – usernames, passwords, even those little cookie files that websites use to remember you. It’s like having a digital pickpocket rummaging through your stuff. According to a Cybernews report, this is a major source of the problem. It’s not just old data either; these infostealers are constantly harvesting new information in real-time.
Credential Stuffing and Repackaged Leaks
It’s not just malware though. A lot of the data comes from credential stuffing attacks. Basically, hackers take old lists of usernames and passwords from previous breaches and try them out on different websites. If people reuse passwords (and a lot of us do!), it works. Plus, there are "repackaged leaks" floating around. These are just collections of data from various sources, bundled together and sold or shared online. It’s like a digital recycling center for stolen information. This password exposure is a serious issue.
Misconfigured Servers and Cloud Storage Vulnerabilities
And here’s a scary part: sometimes, the data isn’t even stolen through sophisticated hacking. A lot of it is just sitting out in the open because of misconfigured servers and cloud storage. Think of it like leaving your front door wide open. Companies mess up their security settings, and suddenly, huge databases of sensitive information are accessible to anyone who knows where to look. It highlights a serious lapse in cybersecurity practices. It’s crazy how often this happens. It’s like companies aren’t even trying sometimes. This significant cybersecurity risk needs to be addressed immediately.
Deep Dive Into the Compromised Data

Social Media and Corporate Service Exposure
Okay, so what kind of stuff are we talking about here? Well, pretty much everything. The breach hits all the major digital services. Think about it: if you use it, it’s probably affected. We’re talking about:
- Social media platforms like Facebook, Telegram, and even Twitch.
- Corporate services, including GitHub and a bunch of cloud providers.
- Email platforms – basically, anything you use for work or personal stuff.
It’s a mess, honestly. It’s not just one platform; it’s a widespread issue. This AI in cybersecurity situation is getting out of hand.
Government and Financial Portal Breaches
It’s not just social media and your work email that are at risk. Government and financial portals are also in the mix. Imagine the kind of data stored there – social security numbers, bank account details, tax information. It’s a goldmine for identity thieves. The scale of this is just insane. It makes you wonder where is safe to store your data anymore. I’m starting to think we should all go back to writing letters and keeping our money under the mattress.
Sensitive User Information at Risk
At the end of the day, it all boils down to this: your sensitive user information is at risk. Usernames, passwords, security questions, maybe even your mother’s maiden name. All that stuff you try to keep secret? Yeah, it’s potentially out there. And it’s not just old data; some of it is recent, making it even more dangerous. It’s like these hackers are getting better and faster at stealing our info. I’m not sure what the solution is, but we need to figure it out fast. Maybe it’s time to ditch passwords altogether and switch to something more secure. I heard passkeys are good, but who knows? It’s all so confusing.
Why This Security Leaks News is Different
Okay, so you might be thinking, "Another data breach? What’s new?" But trust me, this one feels different. It’s not just the size of it, although 16 billion passwords exposed is pretty wild. It’s how the data is being collected and how recent it is that makes this particularly alarming.
Real-Time Data Harvesting by Infostealers
What sets this apart from your run-of-the-mill data dump is the freshness of the information. Infostealer malware is grabbing data in real-time. We’re not talking about old databases being resurfaced; this is active harvesting. It’s like someone is constantly vacuuming up your passwords and personal info as you type them. This means the data is more accurate and, unfortunately, more useful for attackers.
New Datasets Appearing Frequently
It’s not a one-time event. New, massive datasets are popping up every few weeks. One dataset, possibly linked to the Portuguese-speaking community, had something like 3.5 billion records. Another, labeled "Telegram", contained 60 million entries. It’s a never-ending stream of compromised data. It’s like trying to bail water out of a sinking ship with a spoon. Here’s a quick look at the scale:
- Dataset A: 3.5 Billion Records (Portuguese-Speaking Community?)
- Dataset B: 60 Million Records (Telegram)
- Dataset C: Unknown (Labeled "Logins")
- Dataset D: Unknown (Labeled "Credentials")
Targeted Community Breaches
These breaches aren’t always random. There’s evidence of targeted attacks on specific communities. This means attackers are becoming more sophisticated in who they target. It’s not just about casting a wide net; it’s about finding the right fish. The cybersecurity breach is a blueprint for mass exploitation.
The Broader Implications of Security Leaks News
Roadmap for Exploitation and Identity Theft
This isn’t just a leak; it’s a blueprint for exploitation. The sheer volume of exposed data creates a roadmap for malicious actors. The datasets contain fresh, structured information that’s perfect for phishing campaigns, identity theft, and account takeovers. It’s like handing criminals a detailed guide to exploit vulnerabilities.
Increased Risk of Account Takeovers
With billions of usernames and passwords exposed, the risk of account takeovers skyrockets. Imagine someone gaining access to your email, social media, or bank account. It’s a nightmare scenario that becomes much more likely when credentials are leaked. The major data breaches we’ve seen recently only amplify this threat. It’s not just about individual accounts either; businesses are also at risk.
Fueling Ransomware and Business Email Compromise
Leaked credentials can be used to gain initial access to systems, paving the way for ransomware attacks and business email compromise (BEC). Once inside, attackers can encrypt data and demand ransom or impersonate employees to steal money. It’s a domino effect that starts with a single compromised password. The consequences can be devastating, leading to financial losses, reputational damage, and operational disruptions. It’s a serious problem, and it’s only getting worse. Here’s a quick look at how these attacks can play out:
- Attackers use leaked credentials to access a company’s network.
- They deploy ransomware, encrypting critical data.
- The company is forced to pay a ransom to regain access to its data.
- Alternatively, attackers use compromised email accounts to send fraudulent invoices or wire transfer requests.
- Employees unknowingly transfer funds to the attackers’ accounts.
Timeline of Significant Security Leaks News

Mother of All Breaches (MOAB) in 2024
Okay, so the "Mother of All Breaches," or MOAB as it’s called, happened in 2024. This thing was HUGE – like, 26 billion records huge. It’s not just a bunch of random stuff; it’s a collection of data from tons of other breaches, making it a super useful tool for bad guys. It’s like they’re building a giant cheat sheet for hacking. You can read more about cyber attacks on TechAnnouncer.
RockYou2024 and Password Exposure
Then there’s RockYou2024. Sounds like a music festival gone wrong, but it’s actually a massive password dump. We’re talking nearly 10 billion unique passwords exposed. The scary part? People reuse passwords all the time, so if your password was in this leak, it’s probably compromised on multiple sites. Time to change those passwords, folks! It’s a good idea to use a password manager to generate strong, unique passwords.
China Leak and Financial Records
And don’t forget the China Leak. This one involved billions of financial and personal records, mainly through WeChat and Alipay. Imagine all that sensitive data just floating around. It’s a goldmine for identity theft and financial fraud. This is a good reminder to enable Multi-Factor Authentication wherever possible.
Responding to the Latest Security Leaks News
Okay, so all this security leaks news is pretty scary, right? What can we actually do about it? It feels like we’re constantly hearing about these massive breaches, and it’s easy to feel helpless. But there are definitely steps we can take to protect ourselves. It’s not a perfect solution, but it’s better than just sitting around waiting to get hacked.
Urgent Password Changes Recommended
First things first: change your passwords. I know, I know, it’s a pain. But seriously, if you’re using the same password for multiple accounts (and let’s be honest, most of us are), now is the time to switch things up. Think about it: if one of your accounts gets compromised, hackers can then try that same password on all your other accounts. Use a password manager to generate strong, unique passwords for each site. It makes life so much easier, and it’s way more secure. I personally use one, and it’s a lifesaver.
FBI Warnings on SMS Phishing
The FBI has been putting out warnings about SMS phishing, also known as "smishing." Basically, you get a text message that looks like it’s from a legitimate company, like your bank or a delivery service. They’ll ask you to click a link or provide some personal information. Don’t do it! These messages are designed to steal your information. Always go directly to the company’s website or app to check on your account. If you get a suspicious text, report it to the FBI. It’s better to be safe than sorry. I got one the other day pretending to be from the DMV, asking me to update my address. I knew it was fake because I had just updated it last week!
The Role of Passkeys in Enhanced Security
Okay, so passwords are kind of old news. The future of security is passkeys. What are passkeys? They’re basically a more secure way to log in to your accounts. Instead of using a password, you use your fingerprint, face scan, or a PIN on your device. This makes it much harder for hackers to steal your login information. Passkeys are still relatively new, but more and more websites and apps are starting to support them. If you have the option to use a passkey, definitely do it. It’s a game-changer. I’m slowly switching all my accounts over to passkeys, and it’s a huge relief knowing that my accounts are more secure. It’s like having a super-strong lock on your front door. Plus, you don’t have to remember a complicated password! It’s a win-win.
Wrapping It Up
So, what’s the big takeaway from all this? Well, these data leaks are a pretty big deal, and they keep happening. It’s not just about some big company messing up; it’s about our own info floating around out there. We’ve gotta be smart about our online habits, like using strong passwords and watching out for weird emails. The folks trying to steal our data are always finding new ways, so staying a step ahead is key. It’s a bit of a pain, sure, but keeping our digital lives safe is totally worth the effort.
Frequently Asked Questions
What exactly is this huge data leak?
This massive leak includes over 16 billion pieces of login information. It’s like finding a giant puzzle with billions of pieces, each one a username or password.
Where did all this stolen information come from?
This data didn’t come from one single hack. Instead, it was collected from many different places, mostly from bad software called ‘infostealers’ that sneak onto computers and steal info. Some of it also came from old leaks that were put back together, or from online storage that wasn’t properly locked down.
What kind of personal information was stolen?
A lot of different things are in these stolen records. We’re talking about login details for social media sites like Facebook, Google, and Telegram, plus work accounts like GitHub. Even information from government websites and banks was found, putting lots of personal details at risk.
Why is this particular leak such a big deal compared to others?
This leak is different because much of the data is brand new, not just old stuff recycled. Infostealer programs are constantly grabbing fresh information, so new batches of stolen data show up all the time. This makes it much more dangerous for people.
How can this stolen data be used against people?
This stolen data can be used by bad guys for many harmful things. They can pretend to be you online, take over your accounts, or send you tricky messages to get even more information. It also helps them with bigger crimes like ransomware attacks, where they lock up computers and demand money.
What should I do to protect myself after hearing about this?
To protect yourself, you should immediately change your passwords, especially for important accounts. The FBI is also warning people about fake text messages, so be careful what links you click. Using ‘passkeys’ is a good idea too, as they are a more secure way to log in without traditional passwords.