In today’s digital world, cyber resilience is more important than ever. Organizations need to be ready for cyber attacks, which can happen at any time. Cyber resilience means not just protecting against these attacks but also being able to bounce back quickly after they occur. This article will explore how businesses can prepare for and recover from cyber threats, focusing on the importance of having a solid strategy, employee training, and the right technology in place.
Key Takeaways
- Cyber resilience is about preparing for, responding to, and recovering from cyber attacks.
- Having a plan in place can help organizations recover faster from incidents.
- Training employees regularly is key to preventing attacks like phishing.
- Using advanced technology can help detect threats before they cause damage.
- Creating a culture of resilience within the organization ensures everyone is on the same page.
Understanding Cyber Resilience
Defining Cyber Resilience
Cyber resilience is the ability of an organization to prepare for, respond to, and recover from cyber incidents. It combines elements of cybersecurity with business continuity to ensure that operations can continue even during adverse events.
Key Components of Cyber Resilience
To build effective cyber resilience, organizations should focus on the following key components:
- Risk Management: Regularly assess and manage risks to identify vulnerabilities.
- Incident Response: Develop a clear plan for responding to cyber incidents.
- Continuous Improvement: Learn from past incidents to enhance future responses.
| Component | Description |
|---|---|
| Risk Management | Identifying and mitigating potential risks. |
| Incident Response | Procedures for handling cyber incidents. |
| Continuous Improvement | Adapting strategies based on lessons learned. |
Cyber Resilience vs. Cybersecurity
While cybersecurity focuses on preventing attacks, cyber resilience emphasizes the ability to recover quickly from them. Here are some differences:
- Focus: Cybersecurity is about defense; cyber resilience is about recovery.
- Approach: Cybersecurity aims to block threats; cyber resilience prepares for when threats succeed.
- Outcome: Cybersecurity seeks to prevent breaches; cyber resilience ensures operations can continue despite them.
Cyber resilience is essential because it helps organizations minimize the impact of attacks and maintain trust with customers.
In summary, understanding cyber resilience is crucial for organizations to effectively navigate the challenges posed by cyber threats. By focusing on preparation, response, and recovery, businesses can ensure they remain operational even in the face of adversity.
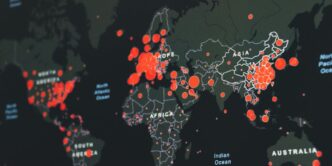
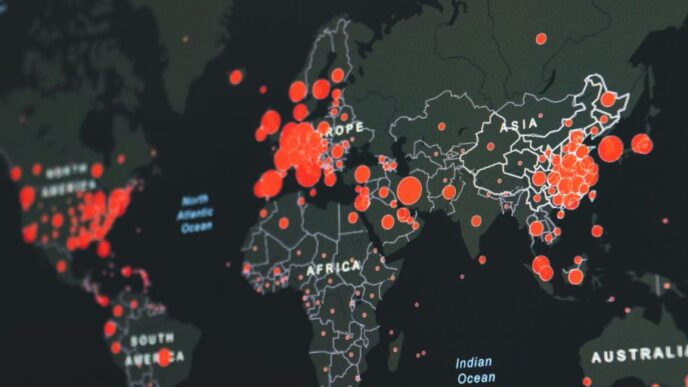
The Growing Threat of Cyber Attacks
Ransomware and Its Impact
Ransomware is a dangerous type of malware that locks up a victim’s data until a ransom is paid. Over the last few years, ransomware attacks have increased significantly. Cybercriminals are now targeting organizations of all sizes, demanding high ransoms for decryption keys. The effects of ransomware can be severe:
- Financial Losses: Paying ransoms and losing business during downtime can hurt an organization financially.
- Data Loss: Even if the ransom is paid, there’s no guarantee that data will be fully restored. Attackers may delete or expose sensitive information.
- Reputational Damage: A ransomware attack can damage customer trust and harm an organization’s reputation, especially if sensitive data is compromised.
- Regulatory Consequences: Organizations may face fines and legal action if they fail to protect sensitive data, especially under regulations like GDPR or CCPA.
Phishing and Social Engineering
Phishing is another common tactic used by cybercriminals. They trick individuals into revealing personal information or clicking on harmful links. Here are some key points about phishing:
- Email Scams: Attackers often send fake emails that look real to steal information.
- Urgency Tactics: Many phishing attempts create a sense of urgency to trick victims into acting quickly.
- Social Media Risks: Cybercriminals also use social media to gather information and target individuals.
Advanced Persistent Threats (APTs)
APTs are complex attacks where cybercriminals gain access to a network and remain undetected for a long time. They often target sensitive information and can cause significant damage. Key characteristics include:
- Stealthy Approach: APTs are designed to avoid detection while gathering information.
- Long-Term Goals: Unlike typical attacks, APTs focus on long-term objectives, often targeting valuable data.
- Resource Intensive: These attacks require significant resources and planning, making them particularly dangerous.
Cyber resilience is essential for organizations to not only survive attacks but also to recover and adapt effectively. Building a strong defense is crucial in today’s digital landscape.
Developing a Cyber Resilience Strategy
Conducting a Risk Assessment
To build a strong cyber resilience strategy, organizations must first identify potential risks. This involves:
- Evaluating current security measures.
- Identifying vulnerabilities in systems and networks.
- Assessing the impact of potential cyber threats.
Creating an Incident Response Plan
An effective incident response plan is crucial. It should include:
- Detection of incidents.
- Steps for containment and recovery.
- Clear communication protocols.
Regularly testing and updating this plan ensures it remains effective against evolving threats.
Implementing Continuous Monitoring
Continuous monitoring helps organizations stay ahead of threats. This includes:
- Using advanced tools for real-time threat detection.
- Regularly reviewing security logs.
- Conducting vulnerability assessments to identify weaknesses.
A proactive approach to cyber resilience not only protects your organization but also builds trust with stakeholders.
By following these steps, organizations can create a robust cyber resilience strategy that prepares them for potential attacks and ensures a swift recovery.
Employee Training and Awareness
Importance of Cybersecurity Training
Training employees is essential for building a strong defense against cyber threats. When staff members understand the risks, they can better protect themselves and the organization. Here are some key reasons why training is vital:
- Awareness: Employees learn to recognize potential threats.
- Prevention: Proper training can help prevent attacks before they happen.
- Response: Well-trained staff can respond quickly and effectively during an incident.
Regular Training Programs
Organizations should implement ongoing training programs to keep employees updated on the latest threats and best practices. Consider the following:
- Monthly Workshops: Regular sessions to discuss new threats and strategies.
- Online Courses: Flexible learning options that employees can complete at their own pace.
- Guest Speakers: Invite experts to share insights on current cyber trends.
Simulated Cyber Attack Drills
Conducting drills can prepare employees for real-life scenarios. These exercises help staff practice their response to cyber incidents. Here’s how to implement them:
- Create Scenarios: Develop realistic attack scenarios for practice.
- Evaluate Responses: After drills, review how employees reacted and identify areas for improvement.
- Feedback Sessions: Hold discussions to gather insights and enhance future drills.
Building a culture of awareness and preparedness is crucial for any organization. Regular training and drills can significantly reduce the risk of successful cyber attacks.
Highlight
Incorporating diverse gadgets into training can enhance engagement and effectiveness. Organizations should explore various tools and resources to keep training fresh and relevant.
Technological Solutions for Cyber Resilience
Advanced Threat Detection Tools
Organizations can utilize advanced threat detection tools to identify and respond to potential cyber threats before they escalate. These tools often include:
- Intrusion detection systems (IDS)
- Security information and event management (SIEM) solutions
- Behavioral analytics tools
Automated Incident Response Systems
Automated incident response systems help organizations react quickly to cyber incidents. They can:
- Detect threats in real-time
- Contain breaches automatically
- Initiate recovery processes without human intervention
Data Backup and Recovery Solutions
Having a solid data backup and recovery solution is crucial for any organization. This includes:
- Regularly scheduled backups
- Off-site or cloud-based storage options
- Testing recovery processes to ensure data integrity
Organizations must prioritize their technological solutions to ensure they can withstand and recover from cyber threats effectively.
By implementing these technological solutions, organizations can enhance their cyber resilience and better prepare for potential attacks. Investing in the right tools is essential for maintaining operational continuity.
Building a Culture of Cyber Resilience
Leadership and Governance
Creating a culture of cyber resilience starts at the top. Leaders must prioritize cybersecurity and ensure that it is a core value of the organization. This includes:
- Setting clear expectations for cybersecurity practices.
- Allocating resources for training and technology.
- Regularly communicating the importance of cyber resilience to all employees.
Cross-Department Collaboration
Cyber resilience is not just the responsibility of the IT department. It requires teamwork across all areas of the organization. Here are some ways to encourage collaboration:
- Establish cross-functional teams to address cybersecurity issues.
- Share information about potential threats and best practices.
- Involve different departments in training and drills to ensure everyone understands their role in maintaining security.
Continuous Improvement and Learning
Organizations must adapt to the ever-changing cyber landscape. This means fostering a culture of continuous learning. Consider these steps:
- Regularly update training programs based on new threats.
- Conduct post-incident reviews to learn from mistakes.
- Encourage employees to share their experiences and insights on cybersecurity.
Building a culture of cyber resilience is an ongoing journey. It requires commitment, communication, and collaboration from everyone in the organization.
By focusing on these areas, organizations can create a strong foundation for cyber resilience, ensuring they are better prepared for future challenges.
Highlight: diverse gadgets
Organizations should also stay informed about new tools and technologies that can enhance their cyber resilience efforts.
Regulatory and Compliance Considerations
Understanding Regulatory Requirements
Organizations must be aware of various regulatory requirements that govern cybersecurity practices. These regulations are designed to protect sensitive data and ensure that businesses maintain a high level of security. Key regulations include:
- GDPR (General Data Protection Regulation) for data protection in the EU.
- HIPAA (Health Insurance Portability and Accountability Act) for healthcare data in the U.S.
- PCI-DSS (Payment Card Industry Data Security Standard) for payment processing.
Ensuring Compliance
To ensure compliance with these regulations, organizations should:
- Conduct regular audits to assess compliance status.
- Implement necessary security measures to meet regulatory standards.
- Train employees on compliance requirements and best practices.
Impact of Non-Compliance
Failing to comply with regulations can lead to severe consequences, including:
- Financial penalties that can be substantial.
- Reputational damage that can affect customer trust.
- Legal repercussions that may involve lawsuits.
Organizations must prioritize compliance to not only avoid penalties but also to build trust with their customers and stakeholders. A proactive approach to regulatory requirements can significantly enhance an organization’s cyber resilience.
Measuring Cyber Resilience Effectiveness

Key Metrics to Track
To effectively measure cyber resilience, organizations should focus on several key metrics:
- Mean Time to Detect (MTTD): The average time taken to identify a cyber incident.
- Mean Time to Respond (MTTR): The average time taken to respond to a detected incident.
- Recovery Time Objectives (RTO): The targeted duration to restore services after an incident.
Regular Audits and Assessments
Conducting regular audits and assessments is crucial for understanding the effectiveness of cyber resilience strategies. Here are some steps to follow:
- Perform Vulnerability Assessments: Identify weaknesses in your systems.
- Conduct Tabletop Exercises: Simulate cyberattack scenarios to test response plans.
- Review Incident Response Plans: Ensure that all team members know their roles during a crisis.
Adapting to New Threats
Organizations must remain flexible and ready to adapt to new threats. This can be achieved by:
- Staying Informed: Keep up with the latest cybersecurity trends and threats.
- Continuous Training: Regularly train employees on new threats and response strategies.
- Feedback Loops: Use lessons learned from past incidents to improve resilience strategies.
Effective cyber resilience is not just about defense; it’s about being prepared to recover and adapt quickly.
By focusing on these areas, organizations can better measure their cyber resilience and ensure they are prepared for future challenges. Continuous adversary emulation is essential for staying ahead of potential threats in an evolving digital landscape.
Case Studies of Cyber Resilience
Successful Recovery Stories
Many organizations have faced cyber attacks and emerged stronger. Here are a few notable examples:
- Company A: After a ransomware attack, they implemented a robust backup system, allowing them to recover data without paying the ransom.
- Company B: Following a phishing incident, they enhanced their employee training, leading to a significant drop in successful attacks.
- Company C: They faced an APT but quickly adapted their security measures, improving their overall resilience.
Lessons Learned from Breaches
Organizations can learn valuable lessons from cyber incidents. Key takeaways include:
- Preparation is crucial: Regular training and updated incident response plans can make a difference.
- Invest in technology: Advanced threat detection tools can help identify and mitigate risks early.
- Communication matters: Clear communication during a crisis can help maintain trust with customers and stakeholders.
Best Practices from Industry Leaders
Leading organizations have shared their strategies for building cyber resilience:
- Continuous Monitoring: Regularly assess systems for vulnerabilities.
- Employee Engagement: Foster a culture of security awareness among all staff.
- Collaboration: Work with other organizations to share insights and strategies.
Building cyber resilience is not just about technology; it’s about creating a culture that prioritizes security at every level.
Future Trends in Cyber Resilience
Emerging Technologies
As technology evolves, so do the tools and methods used to enhance cyber resilience. Artificial Intelligence (AI) and Machine Learning (ML) are becoming crucial in identifying threats before they escalate. These technologies can analyze vast amounts of data quickly, helping organizations stay ahead of potential attacks.
Evolving Threat Landscape
The types of cyber threats are constantly changing. Organizations must be aware of new tactics used by attackers, such as sophisticated phishing schemes and ransomware attacks. Keeping up with these trends is essential for maintaining a strong defense.
Preparing for the Future
To effectively prepare for future cyber threats, organizations should:
- Invest in Training: Regular training for employees on the latest threats and best practices.
- Adopt New Technologies: Implement advanced tools for threat detection and response.
- Review and Update Policies: Regularly assess and update cybersecurity policies to reflect the current threat landscape.
Cyber resilience is not just about defense; it’s about learning and adapting to new challenges. Organizations must be proactive in their approach to cybersecurity.
| Trend | Description |
|---|---|
| AI and ML | Use of advanced technologies to predict and prevent attacks. |
| New Attack Vectors | Awareness of evolving tactics used by cybercriminals. |
| Continuous Learning | Emphasis on ongoing training and adaptation to new threats. |
By focusing on these areas, organizations can build a robust cyber resilience strategy that not only protects them but also prepares them for future challenges.
Conclusion
In summary, building cyber resilience is essential for organizations today. It’s not just about preventing attacks; it’s about being ready to respond and recover when they happen. By preparing well, detecting threats early, and having a solid recovery plan, businesses can keep running smoothly even after a cyber incident. This approach not only protects sensitive information but also helps maintain trust with customers and partners. As cyber threats continue to grow, organizations must prioritize resilience to ensure they can bounce back quickly and effectively.
Frequently Asked Questions
What is cyber resilience?
Cyber resilience is the ability of an organization to keep running and recover quickly after a cyber attack.
How does cyber resilience differ from cybersecurity?
Cybersecurity is about preventing attacks, while cyber resilience focuses on how to respond and recover from them.
Why is cyber resilience important?
It helps organizations reduce the impact of attacks and ensures they can keep operating even during tough times.
What are some key components of a cyber resilience strategy?
Key parts include having a response plan, training employees, and using technology to monitor threats.
How can employee training improve cyber resilience?
Training helps employees recognize threats and understand how to respond to them, making the whole organization stronger.
What technologies support cyber resilience?
Tools like advanced threat detection, automated response systems, and data backup solutions help organizations stay resilient.
How can organizations measure their cyber resilience?
They can track metrics like recovery time after an attack, the number of incidents, and how quickly they respond to threats.
What should organizations do to prepare for future cyber threats?
They should stay informed about new threats, regularly update their strategies, and continuously train their teams.